EID-EXP-001 – Evidence
Experiment ID: EID-EXP-001
Category: Baseline
Title: Default Entra ID Tenant Security Posture
Result: Weak default protections
Risk Rating: 🟠 Medium
Evidence Scope
This evidence was collected from a newly created Microsoft Entra ID tenant with no manual security hardening applied.
Tenant Conditions:
- Newly created Entra ID tenant
- No Conditional Access policies configured
- Security Defaults: Enabled
- No custom Identity Protection policies
- No third-party security tools integrated
This evidence validates Entra ID's default security posture before any hardening steps are applied.
Tenant Validation 001-01
EID-EXP-001-Tenant-Overview.png
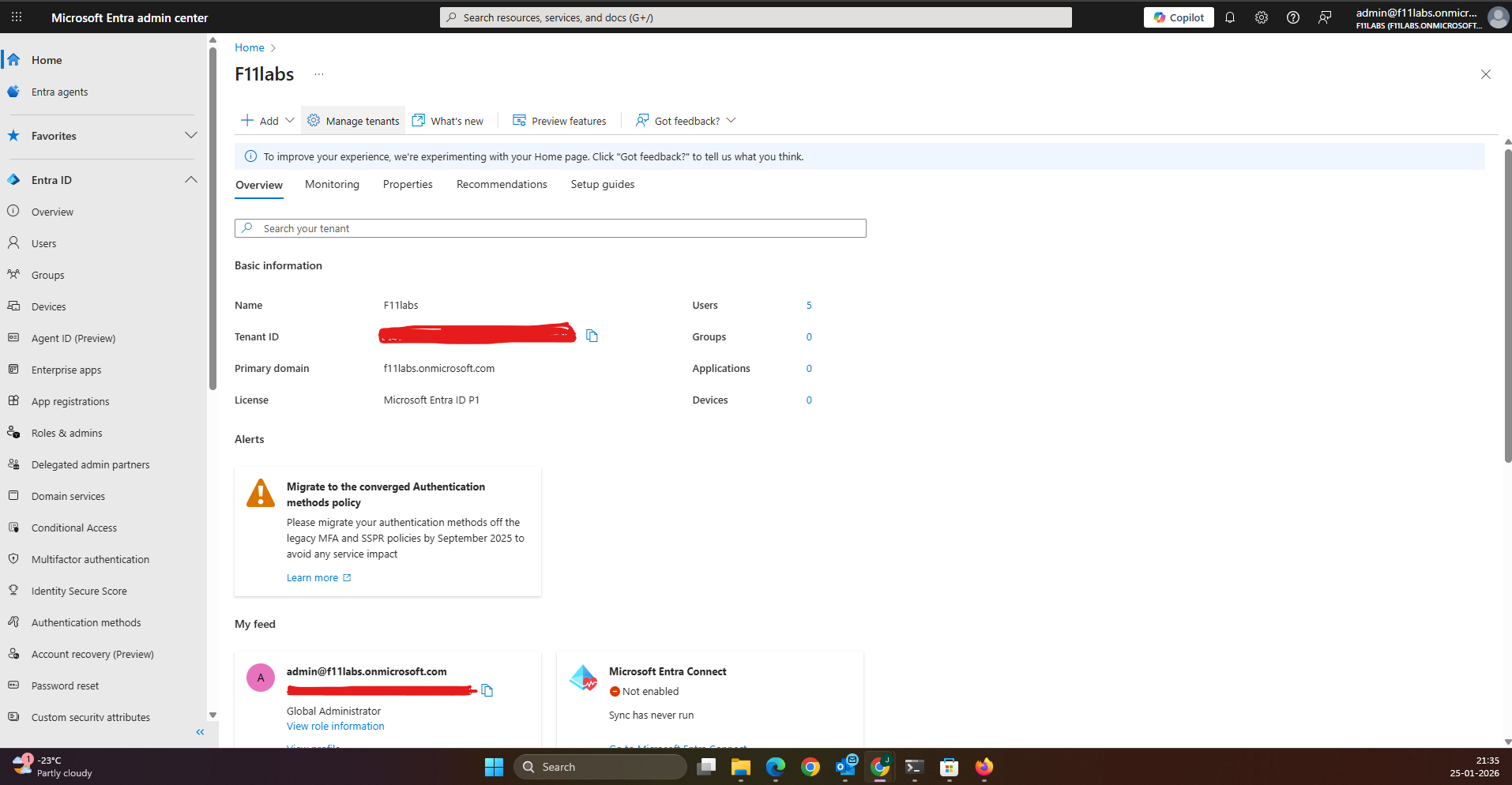
Tenant context validated as F11labs (f11labs.onmicrosoft.com). See Figure EID-EXP-001-Tenant-Overview.png.
Evidence EID-EXP-001-01
Control Area: Conditional Access
Observation: The Conditional Access policy list is empty in the default tenant configuration.
Expected Secure State: At least one Conditional Access policy is enforcing MFA for user sign-ins.
Actual Result: No Conditional Access policies exist by default.
Impact: User sign-ins are not evaluated against explicit access conditions.
Evidence Artifact: EID-EXP-001-01-CA-Empty.png
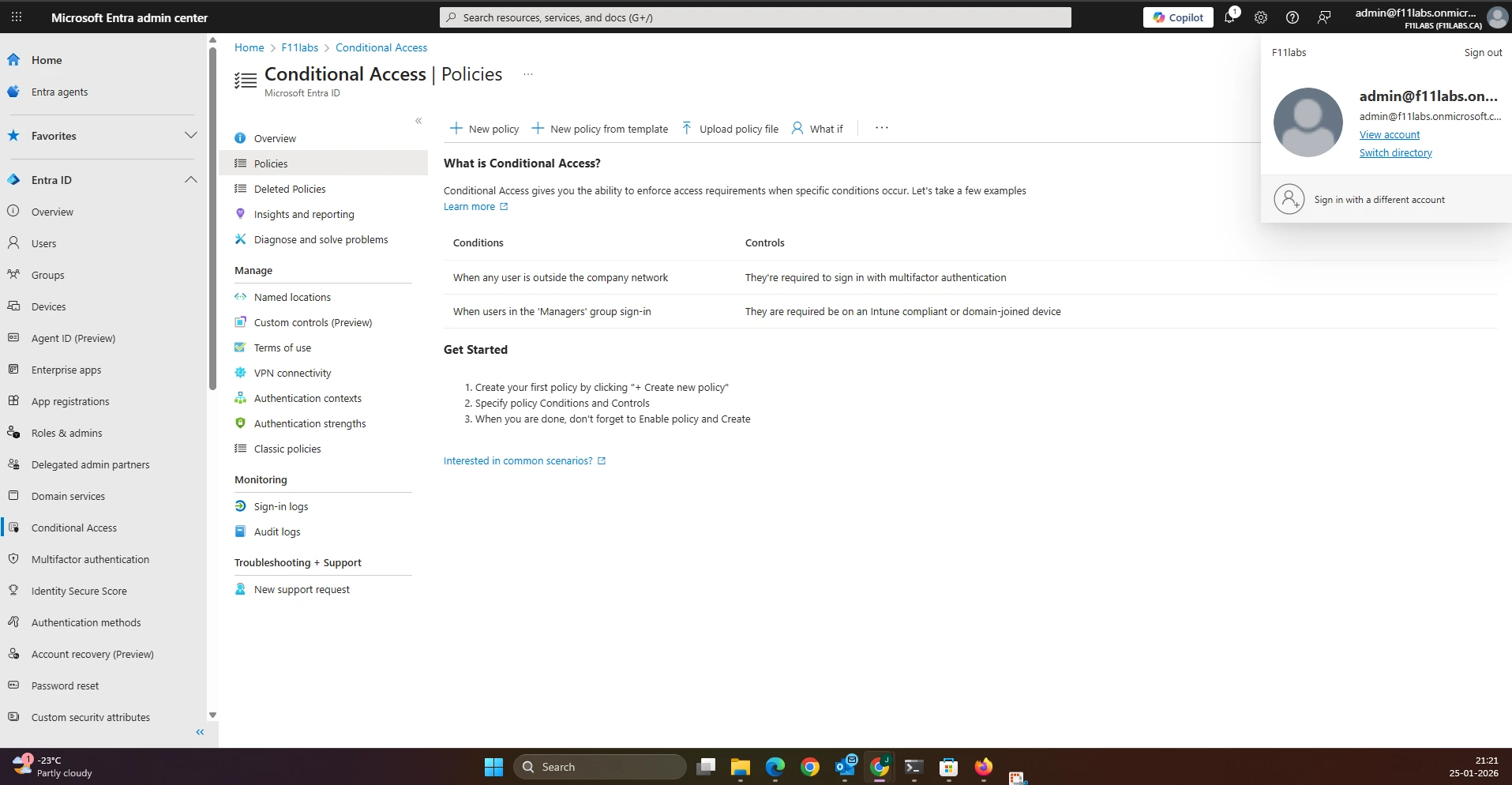
Evidence EID-EXP-001-02
Control Area: Multi-Factor Authentication (MFA)
Observation: A standard user can authenticate successfully without an MFA challenge.
Expected Secure State: MFA is enforced for all interactive user sign-ins.
Actual Result: User authentication succeeds without MFA when Security Defaults are enabled.
Impact: Authentication relies on implicit protections rather than enforceable policy controls.
Evidence Artifact: EID-EXP-001-02-UserLogin-NoMFA.png
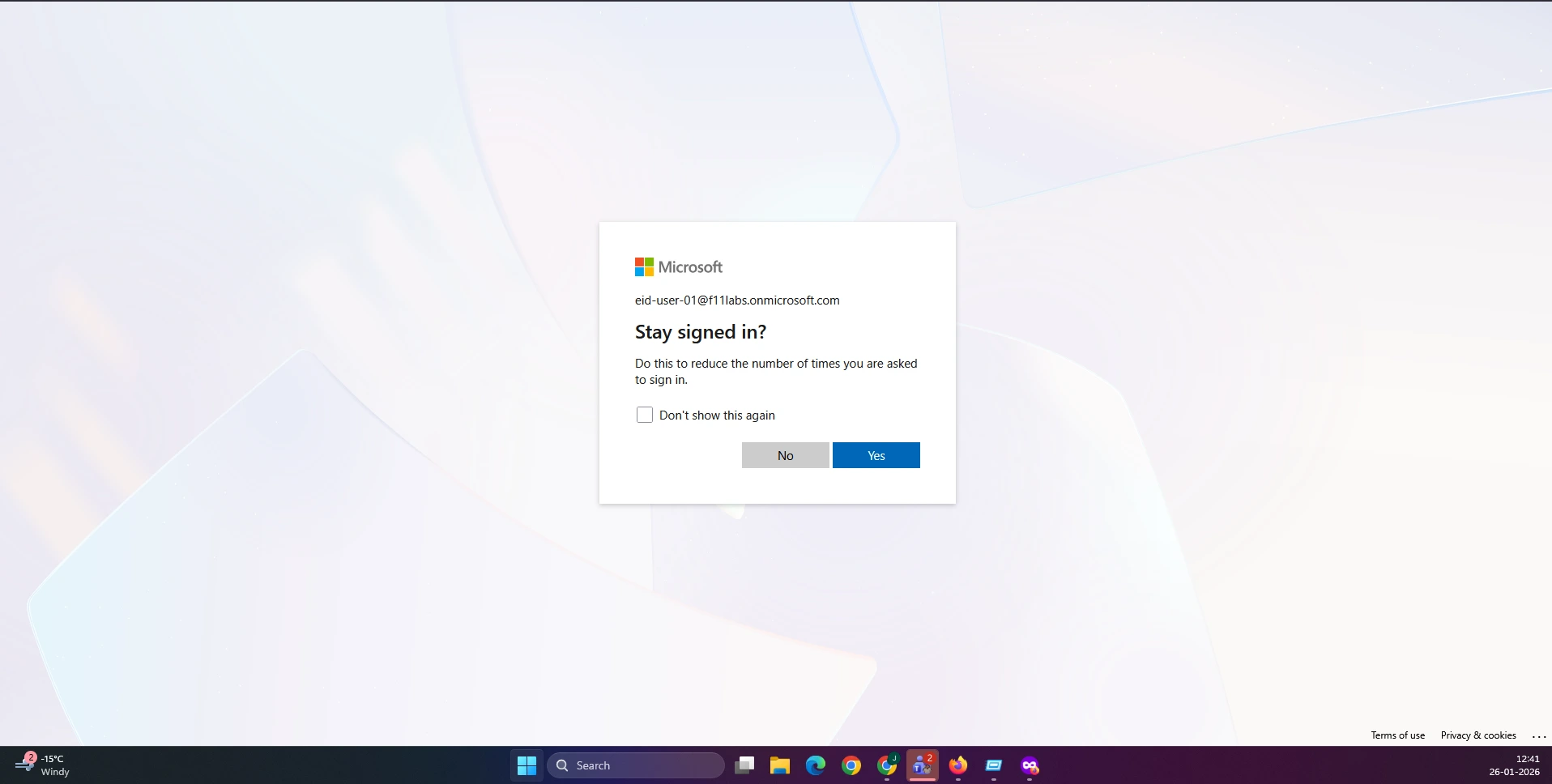
EID-USER-01: User login was successful without MFA. Refer to evidence EID-EXP-001-02-UserLogin-NoMFA.
Evidence Artifact: EID-EXP-001-02-NoAuthenticationMethods.png
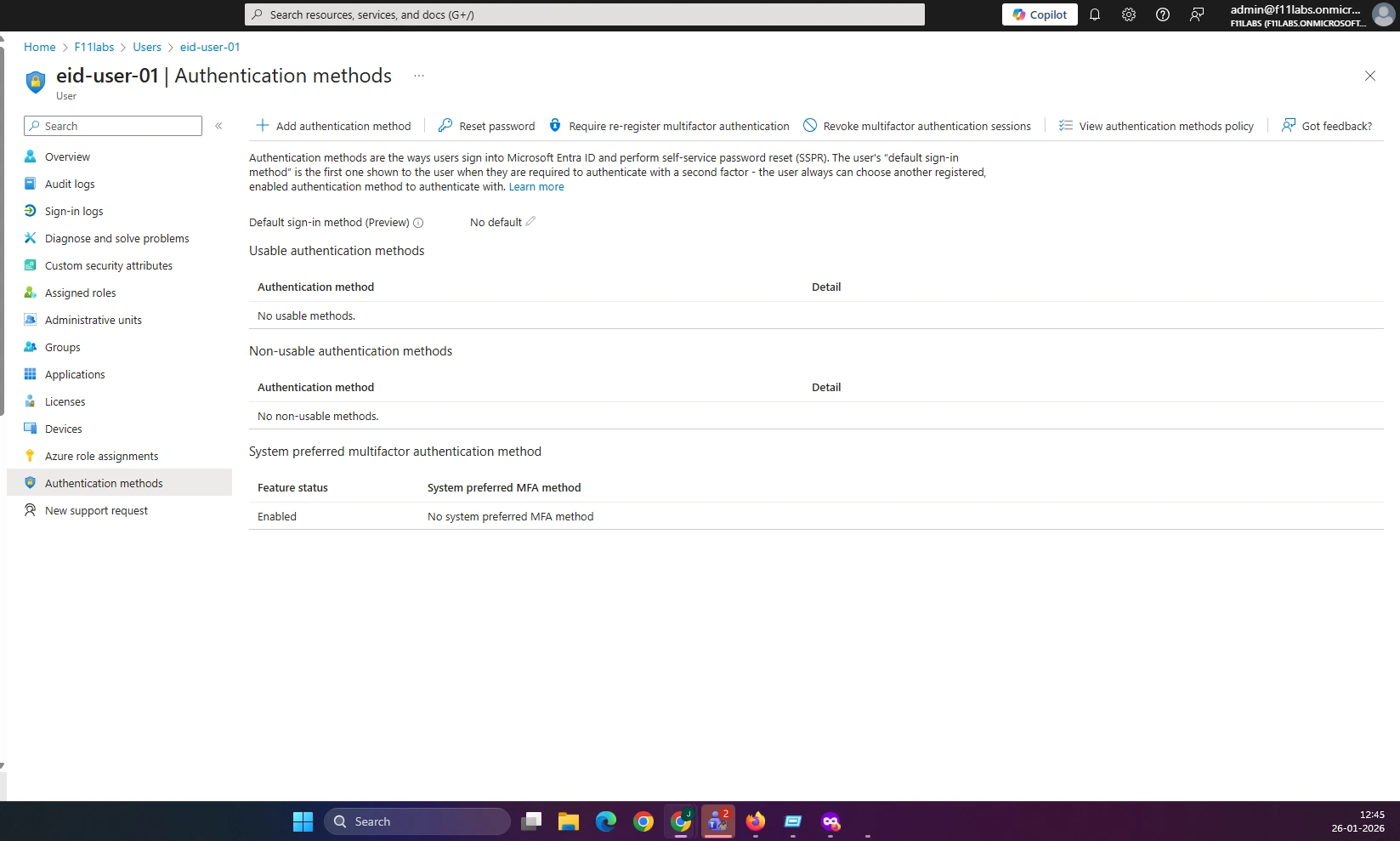
No authentication methods configured for "EID-USER-01". Refer to evidence EID-EXP-001-02-NoAuthenticationMethods.
Evidence EID-EXP-001-03
Control Area: Legacy Authentication
Observation: Legacy authentication is not explicitly blocked via Conditional Access.
Expected Secure State: Legacy authentication should be denied using Conditional Access policies.
Actual Result: No policy exists to explicitly block legacy authentication attempts.
Impact: Password-based authentication attack paths remain available.
Evidence Artifact: EID-EXP-001-03-LegacyAuth-SignInLogs
No Conditional Access policies blocking "Legacy Authentication". Refer to evidence EID-EXP-001-03-LegacyAuth-SignInLogs
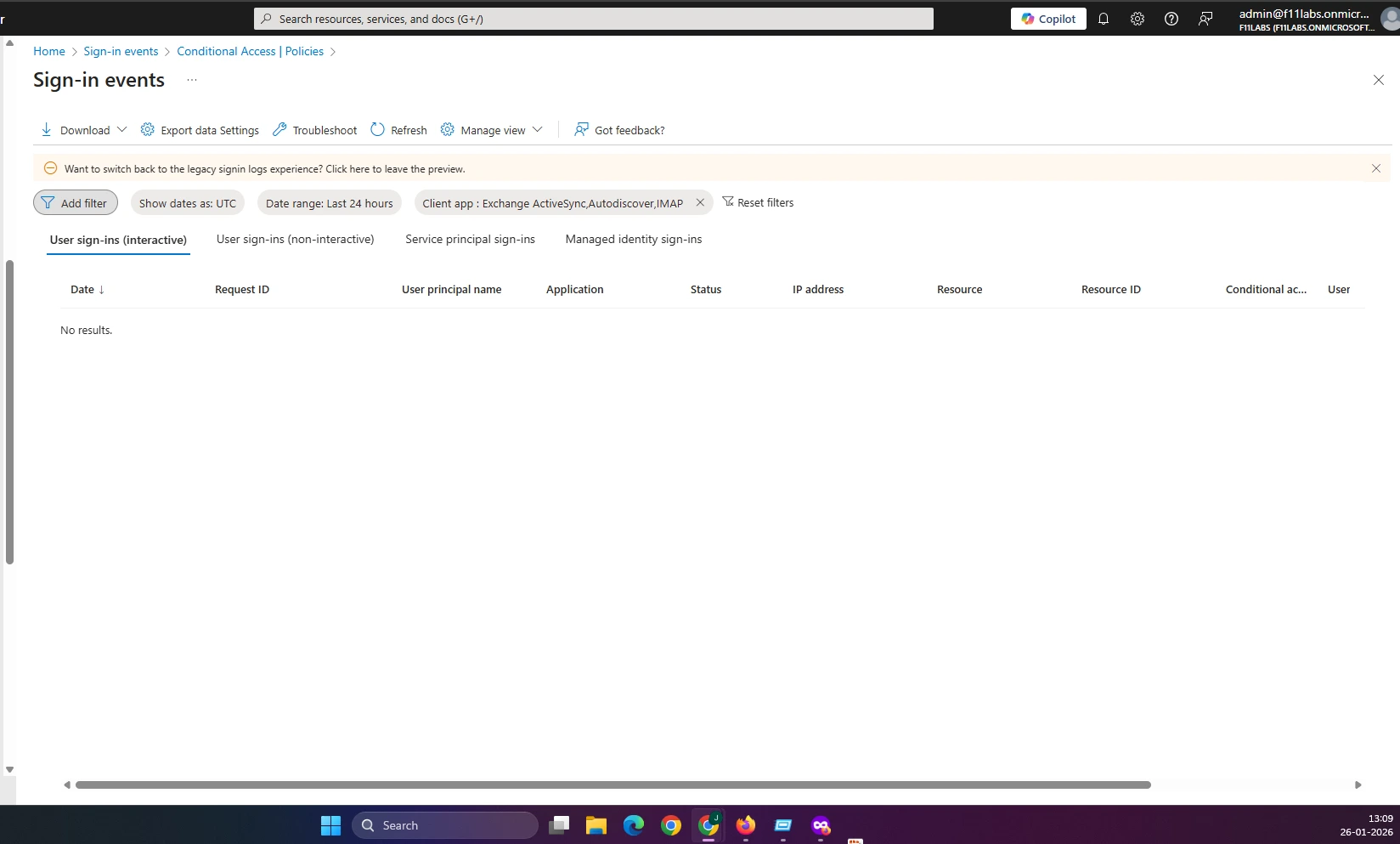
No Conditional Access policy blocks legacy authentication; although no recent legacy sign-ins were observed, the attack path remains available due to lack of explicit enforcement. Refer to evidence EID-EXP-001-03-LegacyAuth-SignInLogs
Evidence EID-EXP-001-04
Control Area: Identity Protection
Observation: No user risk or sign-in risk policies are configured in Identity Protection.
Expected Secure State: Risk-based policies automatically enforce MFA or block access during risky sign-ins.
Actual Result: Identity Protection policies are not enabled by default.
Impact: Risky sign-ins are not automatically mitigated.
Evidence Artifact: EID-EXP-001-04-IdentityProtection-Empty.png
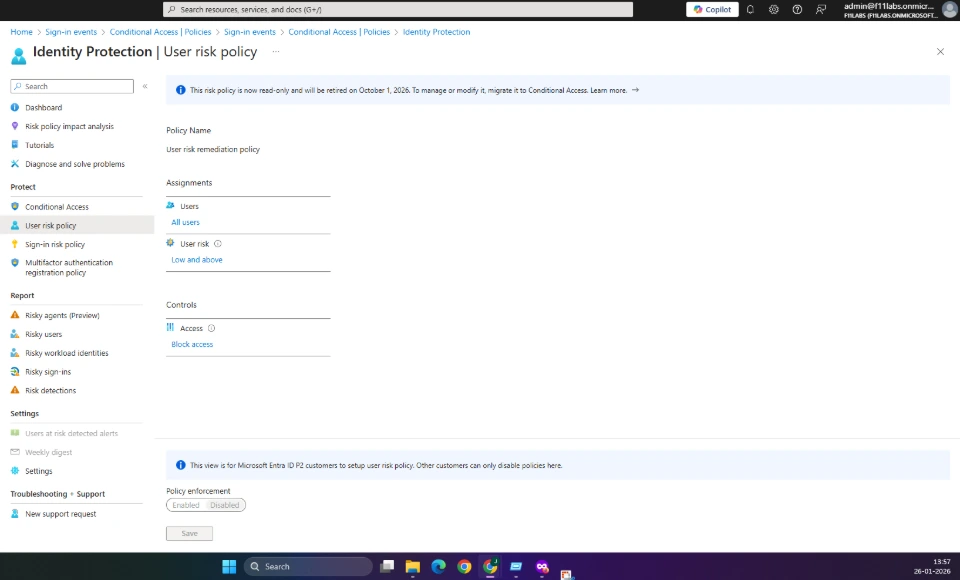
User risk policy is disabled by default. Refer to evidence EID-EXP-001-04-IdentityProtection-Empty.
Evidence EID-EXP-001-05
Control Area: External Identities (Guest Access)
Observation: Guest access is enabled using default external collaboration settings.
Expected Secure State: Guest access is restricted and governed through policy.
Actual Result: Guests can be invited without additional approval or access restrictions.
Impact: External identities increase the tenant attack surface if not governed.
Evidence Artifact: EID-EXP-001-05-GuestAccess-Defaults.png
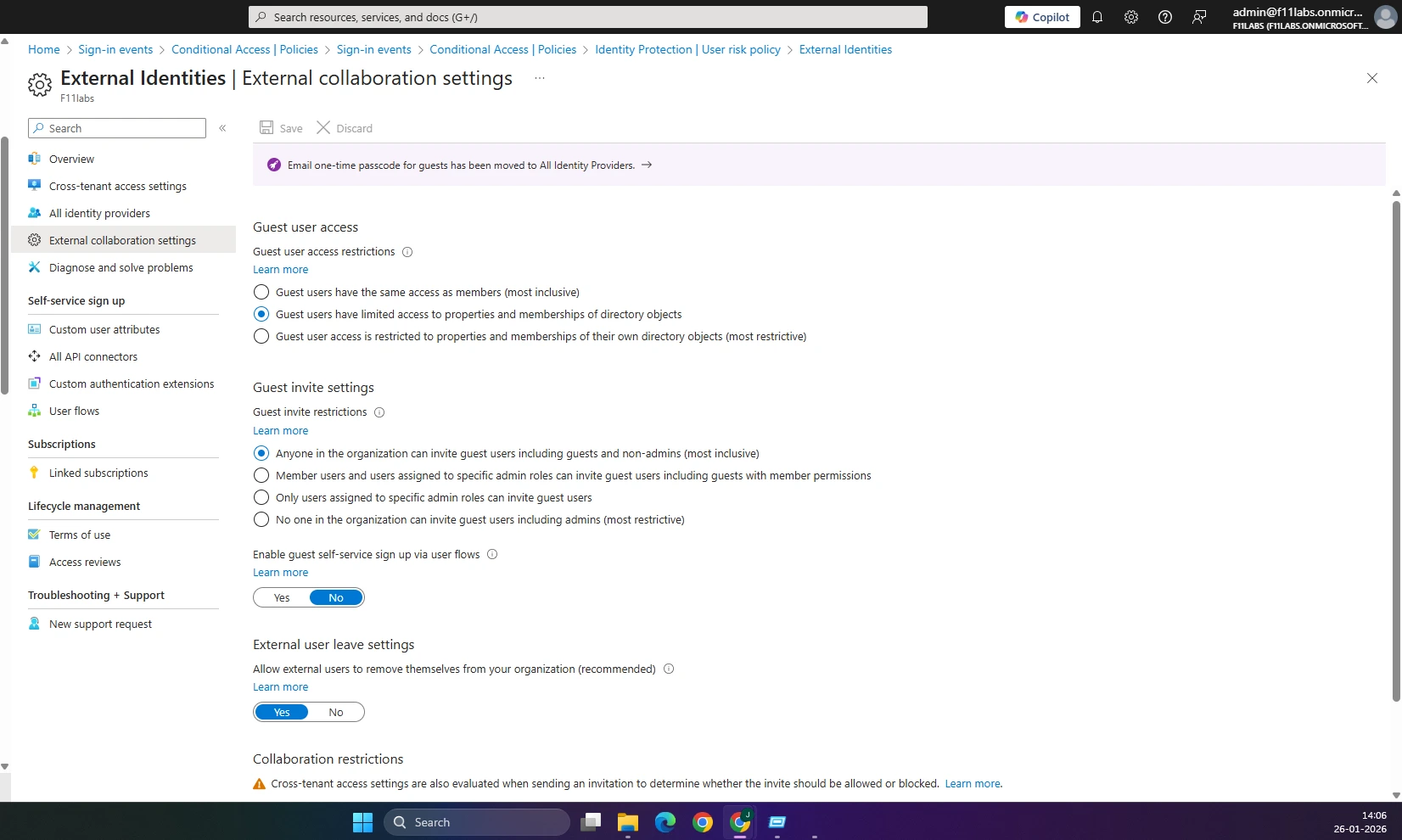
Guests can be invited without additional approval or access restrictions. Refer to evidence EID-EXP-001-05-GuestAccess-Defaults.
Evidence Summary
| Evidence ID | Control Area | Result |
| 001-01 | Tenant Validation | Informational |
| 001-02 | Conditional Access | Weak |
| 001-03 | MFA Enforcement | Weak |
| 001-04 | Legacy Authentication | Weak |
| 001-05 | Identity Protection | Weak |
001-06 | Guest Access | Weak |
Evidence-Based Conclusion
The evidence confirms that a default Microsoft Entra ID tenant relies on implicit protections instead of enforceable security controls. Without explicit Conditional Access, risk-based policies, and legacy authentication blocking, the tenant is exposed to common identity attack paths.
This evidence forms the baseline for subsequent hardening experiments.
Next Experiment: EID-EXP-002 – Microsoft Entra ID Sign-In Logs Deep Dive – Visibility Gaps in Authentication Events
Related Analysis & Fix Guidance
- Technical deep dive: How Legacy Authentication Bypasses Entra ID Security Defaults
- MSP risk & business impact: Why Security Defaults Create False Confidence for SMBs
- Video walkthrough: Real Entra ID Attack: Security Defaults Failed