EID-EXP-003 – Evidence: Break Glass Account Misconfigurations
Experiment ID: EID-EXP-BREAKGLASS
Category: Identity / Emergency Access Controls
Title: Common Break-Glass Account Mistakes and Risk Indicators
Result: Frequent misconfigurations elevate access risks and limit visibility.
Risk Rating: High
Tenant Conditions / Settings (Baseline)
- Microsoft Entra ID is configured with default logging and alerting.
- Privileged Identity Management is configured.
- Conditional Access policies are implemented.
- Break-glass accounts have been created; however, monitoring is limited.
- Specialized alerts for emergency access sign-ins are not configured.
Tenant Validation 003-01
All evidence in this experiment was collected from the Microsoft Entra ID tenant**F11labs** with primary domain **f11labs.onmicrosoft.com**.
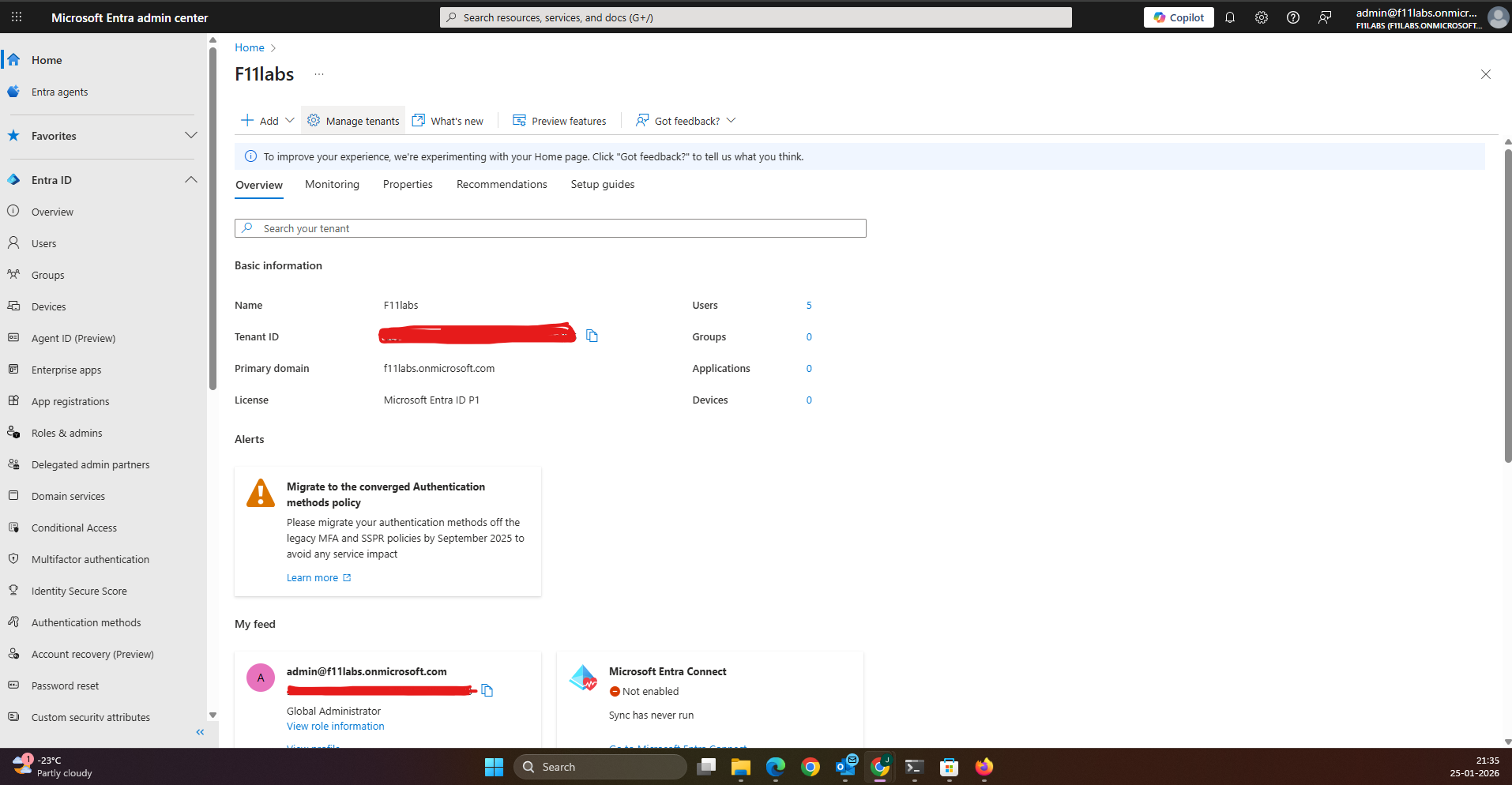
Evidence EID-EXP-003-02 – Missing or Improper Emergency Access Accounts
Control Area: Break Glass Configuration
Observation:
Some environments do not have dedicated emergency access accounts, or these accounts are incorrectly associated with standard user accounts instead of separate cloud-only break-glass accounts.
Expected Secure State:
At least two separate break-glass accounts should be configured as cloud-only Global Administrators, independent of on-premises or federation dependencies.
Actual Result:
Administrators used standard admin accounts that rely on MFA and conditional access. This creates a risk of complete administrative lockout during outages or policy misconfigurations.
Impact:
- No fallback administrative access is available during identity provider outages.
- There is a high risk of lockout if Conditional Access policies misconfigure MFA paths.
- The break-glass function may be unavailable during emergencies.
Evidence Artifacts
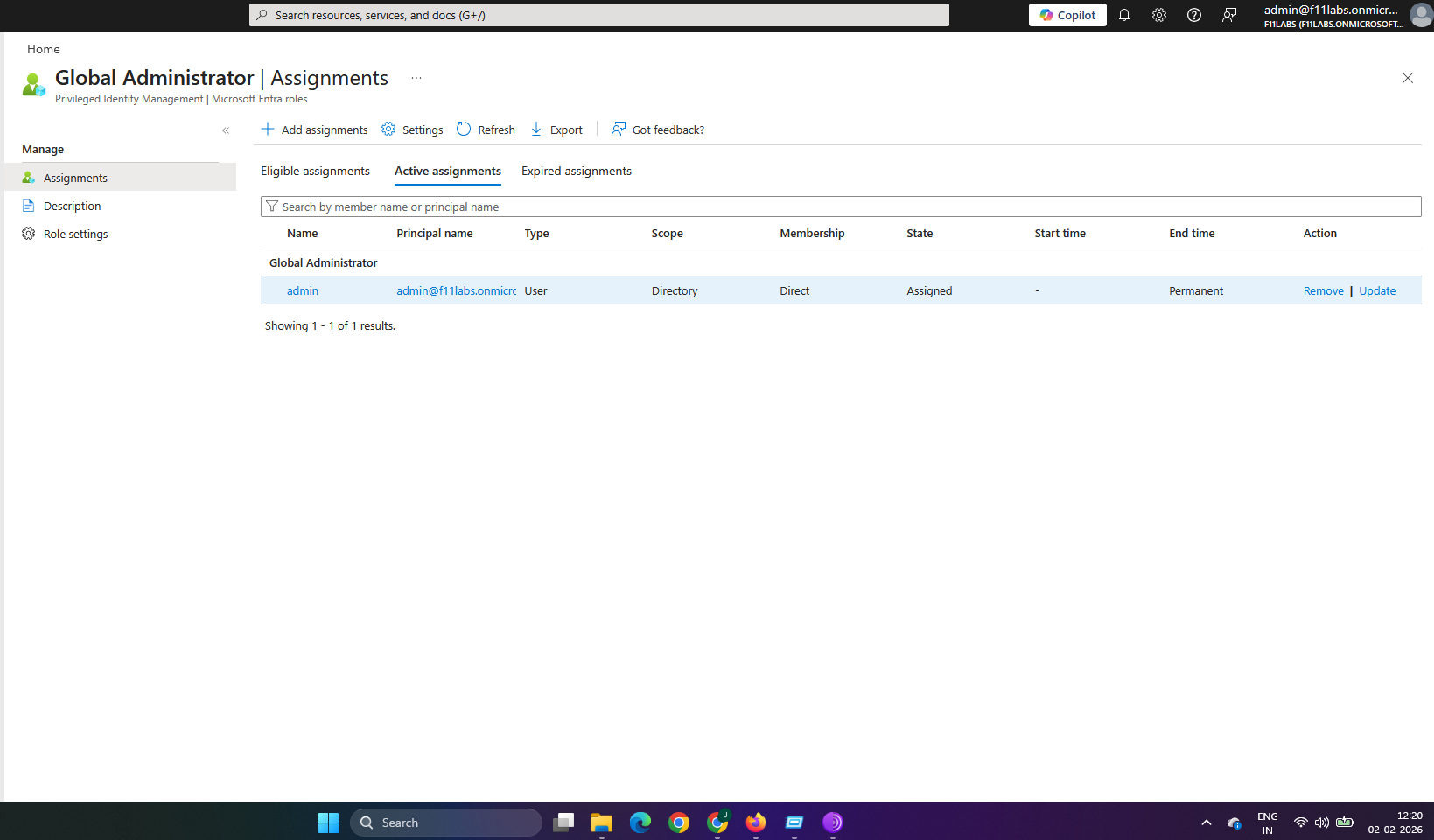
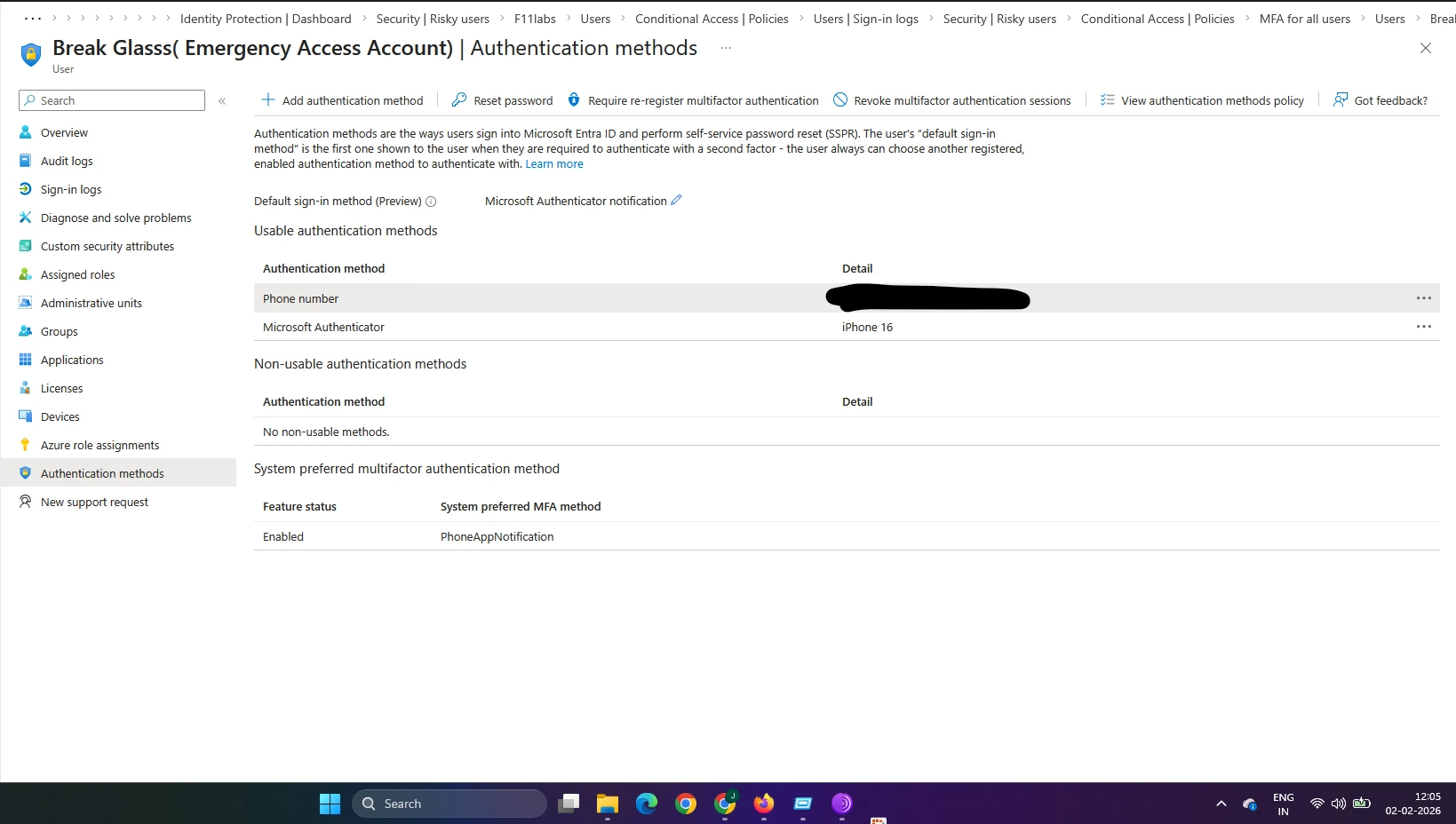
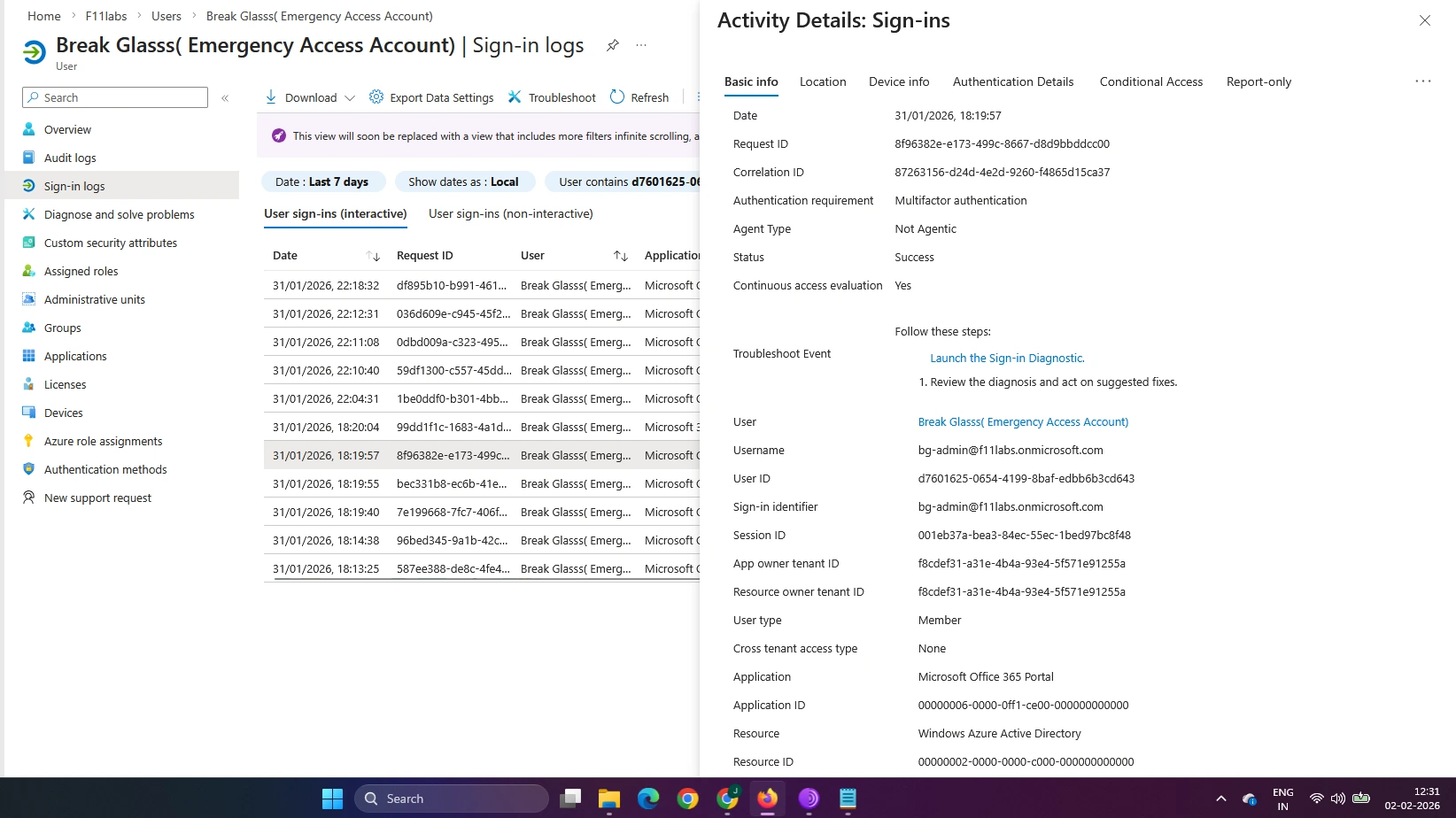
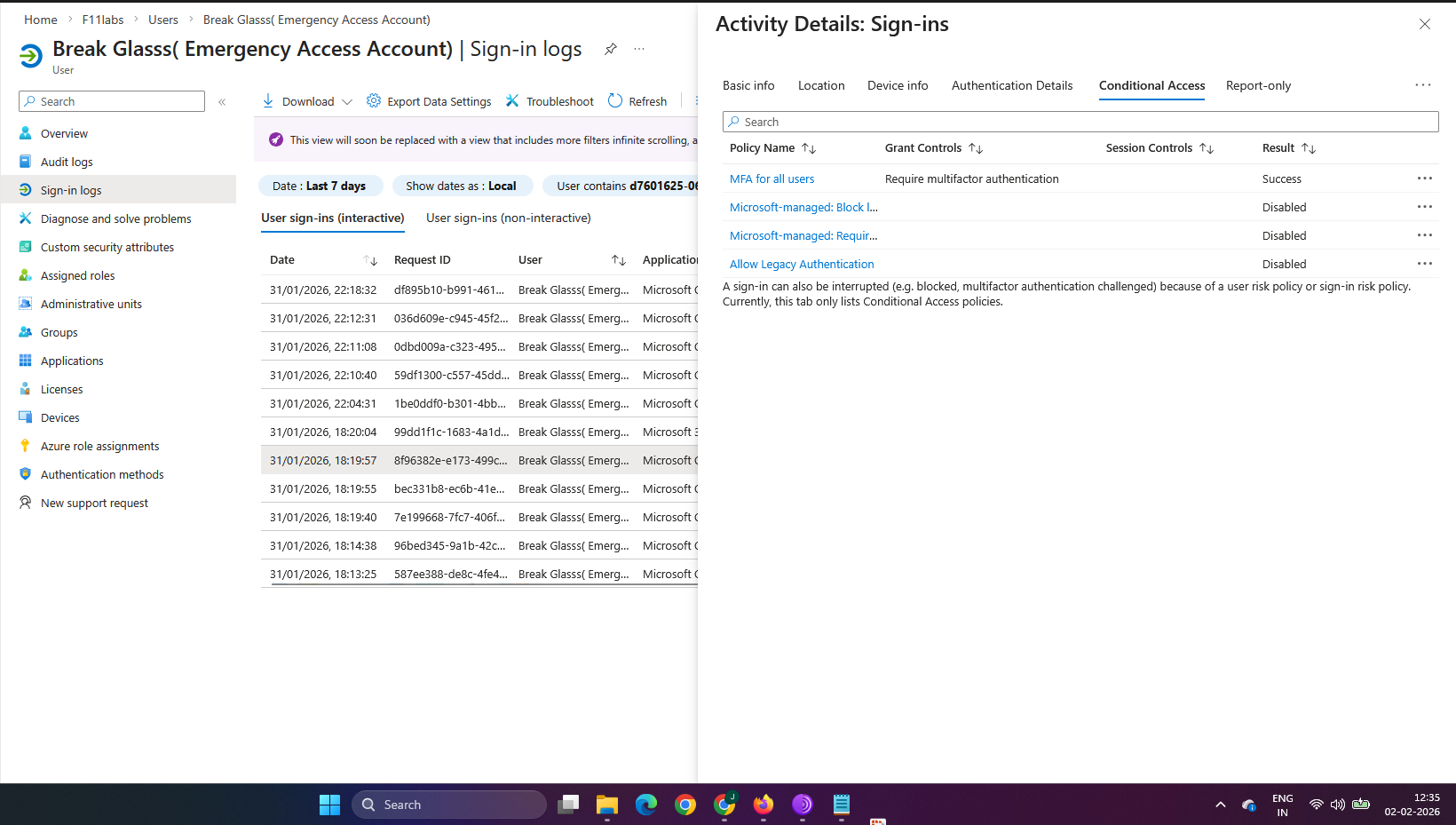
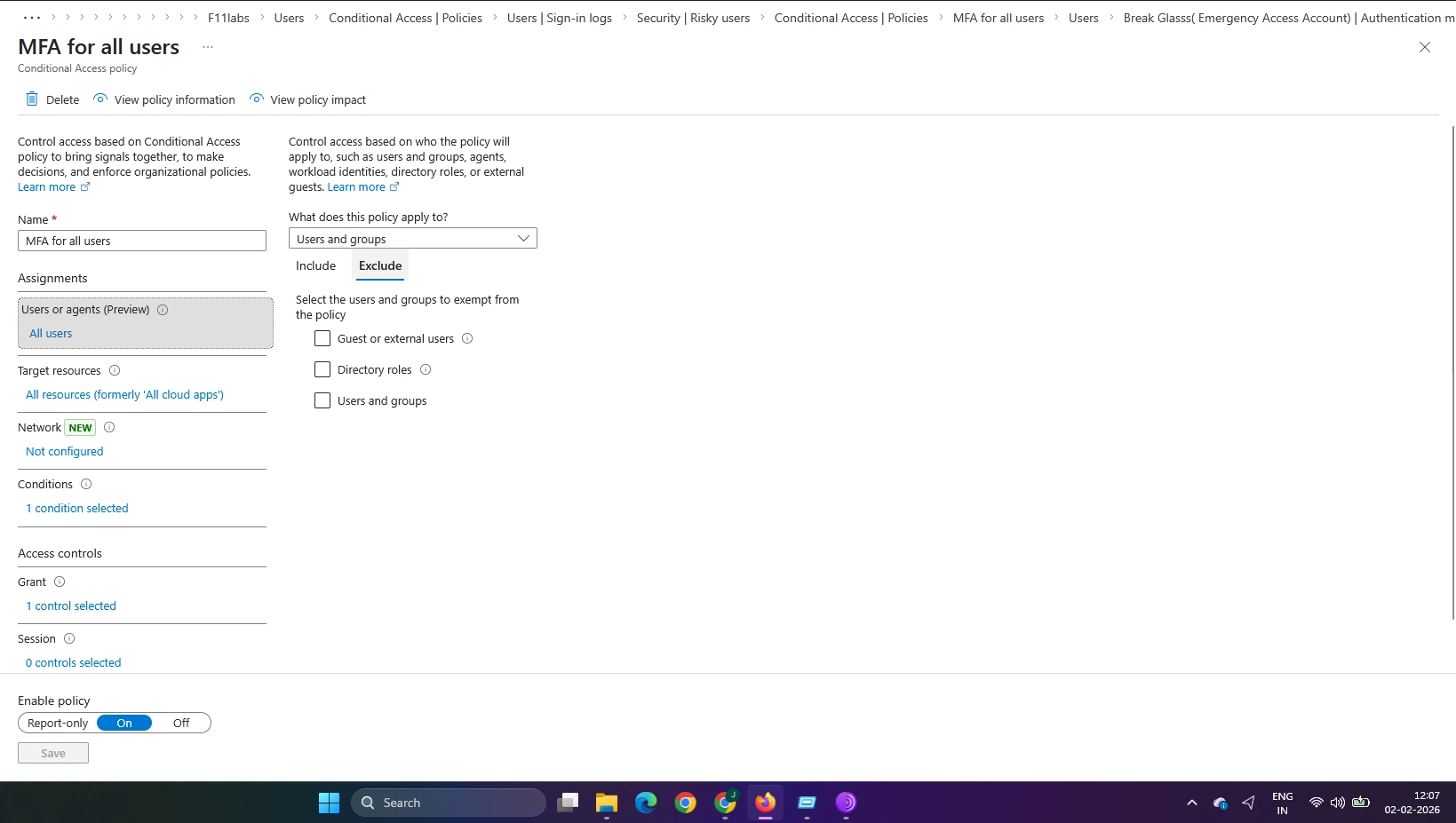
Evidence EID-EXP-003-03 – Overlapping Conditional Access and MFA Policies
Control Area: Policy Scope
Observation
Break-glass accounts were unintentionally included in broad Conditional Access and mandatory MFA policies, subjecting them to the same authentication requirements as standard users.
Expected Secure State:
At least one break-glass account should be excluded from Conditional Access policies to maintain access in the event of misconfiguration or overly restrictive settings.
Actual Result
Emergency access accounts were required to use MFA under Conditional Access, including sign-in risk and location policies. As a result, administrators could be blocked even with valid credentials.
Impact:
- Break-glass accounts lose their effectiveness for emergency access.
- Access may be blocked due to policy misconfiguration.
- Incident responders may be unable to restore administrative control.
Evidence Artifacts
Evidence EID-EXP-003-04 – Shared or Weak Credential Practices
Control Area: Credential Management
Observation:
Break-glass account credentials were stored in unsecured locations, including shared spreadsheets or unsecured vaults, or were accessible to only one administrator.
Expected Secure State:
Credentials should be securely stored in hardware safes or enterprise vaults and distributed among multiple trusted individuals.
Actual Result:
Limiting access to one person or using inadequate storage increases the risk of compromise or loss.
Impact:
- Credentials may be inaccessible if the custodian is unavailable.
- There is an increased risk of credential compromise.
- The break-glass account may become a security liability rather than a safeguard.
Evidence Artifacts
Evidence Summary – Break Glass Mistakes
| 001 | Tenant Validation | Informational |
| 002 | Configuration | Critical – No emergency fallback |
| 003 | Policy Scope | High – CA/MFA blocks access |
004 | Credential Management | Medium – Insecure storage |
Evidence-Based Conclusion
Break-glass accounts are designed for emergency administrative access, but frequent misconfigurations often compromise their effectiveness. Typical issues include missing dedicated accounts, restrictive policy inclusion, inadequate monitoring, and poor credential management. Without proper design and alerting, these accounts may provide a false sense of security and increase risk during emergencies or attacks.
Next Experiment: EID-EXP-004 – Identity Protection Alerts Admins Ignore – Default Alerts Without Enforcement
Related Analysis & Fix Guidance
- Technical deep dive: Break-Glass Accounts in Microsoft Entra ID: Failure Modes, Detection, and Hardening
- MSP risk & business impact: When Break-Glass Accounts Fail: The Hidden Business Risk and Cost for MSPs
- Video walkthrough: Break-Glass Accounts Fail More Than You Think | Entra ID Lockout Risks You Should Test Today