EID-EXP-005 — Evidence
Enforcing Risk Remediation with Conditional Access Policies
Experiment ID: EID-EXP-005
Category: Microsoft Entra ID / Identity Protection / Conditional Access
Objective: Validate that Identity Protection alerts do not enforce remediation unless Conditional Access policies are configured.
Result: Risk-based Conditional Access forces remediation (password reset / MFA) and reduces the risk of persistent identity compromise.
Risk Rating: Critical (if not enforced)
Scope
This experiment demonstrates a security gap: Microsoft Entra Identity Protection detects risk events, but access remains permitted unless risk-based Conditional Access policies are implemented. This lab provides evidence for:
- Risky sign-in detection
- Risky user persistence
- Default behaviour without enforcement
- Remediation enforcement using Conditional Access
Lab Conditions
- Microsoft Entra ID tenant with Entra ID P2
- Identity Protection enabled
- Test user with MFA registered.
- No risk-based Conditional Access policies initially enabled
- Break-glass admin account excluded from policies.
- VPN used to simulate a risky sign-in
Experiment Setup
Accounts
- LAB User: lab-user@tenant.onmicrosoft.com
- Break-glass Admin: bg-admin@tenant.onmicrosoft.com
Tools
- VPN (consumer VPN to simulate sign-in from another country)
- Microsoft Entra Admin Center
- Identity Protection blade
- Conditional Access blade
EID-EXP-005-01 — Evidence: Risky Sign-in Detected but Access Allowed
Control Area
Identity Protection — Risky Sign-ins
Expected Secure Behavior
A risky sign-in should prompt remediation or be automatically blocked.
Observed Behavior
- Risky sign-in is detected and logged.
- MFA is prompted
- User completes MFA
- Sign-in succeeds
- Access is still allowed.
Impact
- Detection works
- Enforcement is not enabled by default.
- A compromised session may still be successful..
Evidence Artifact
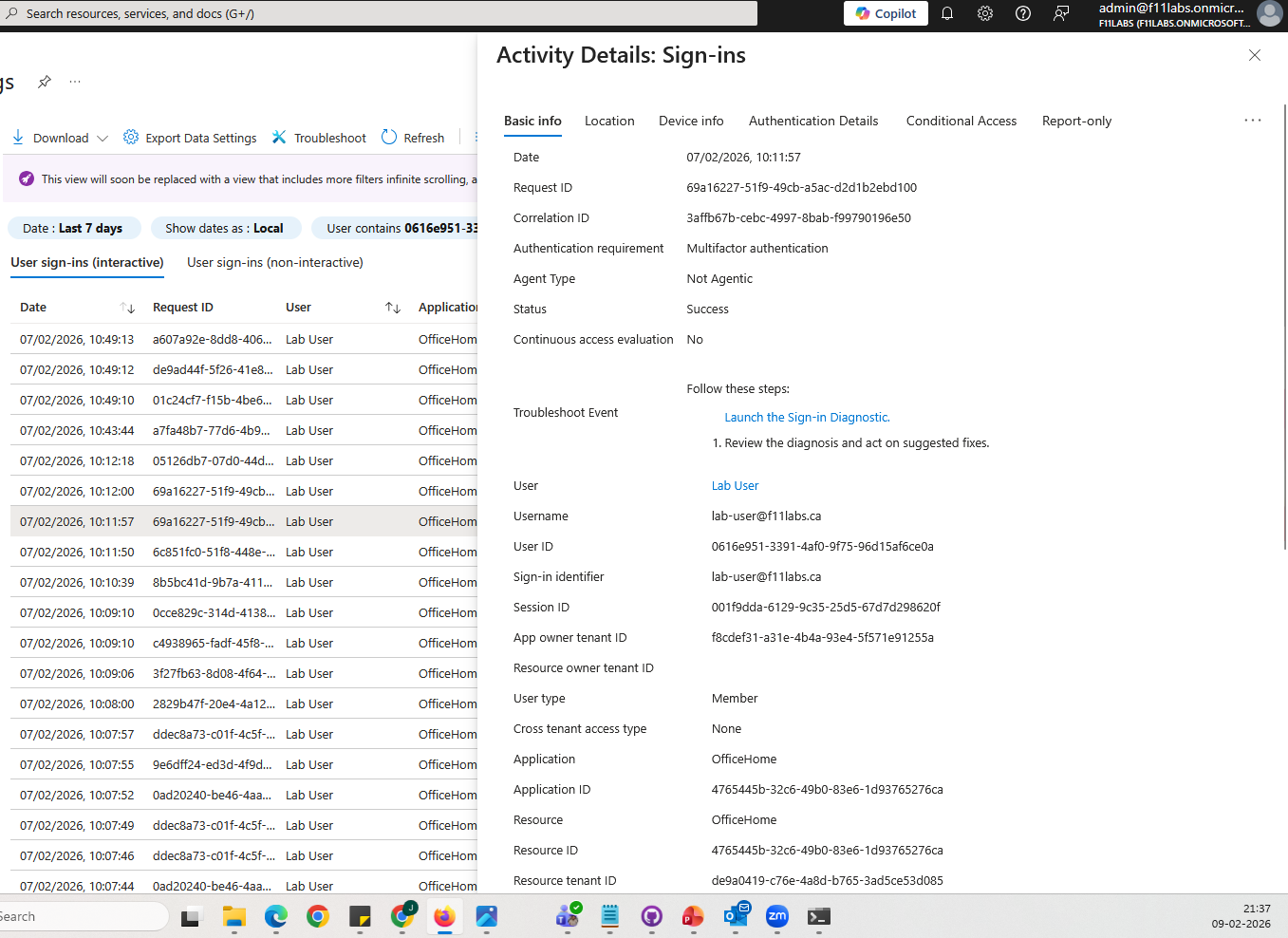
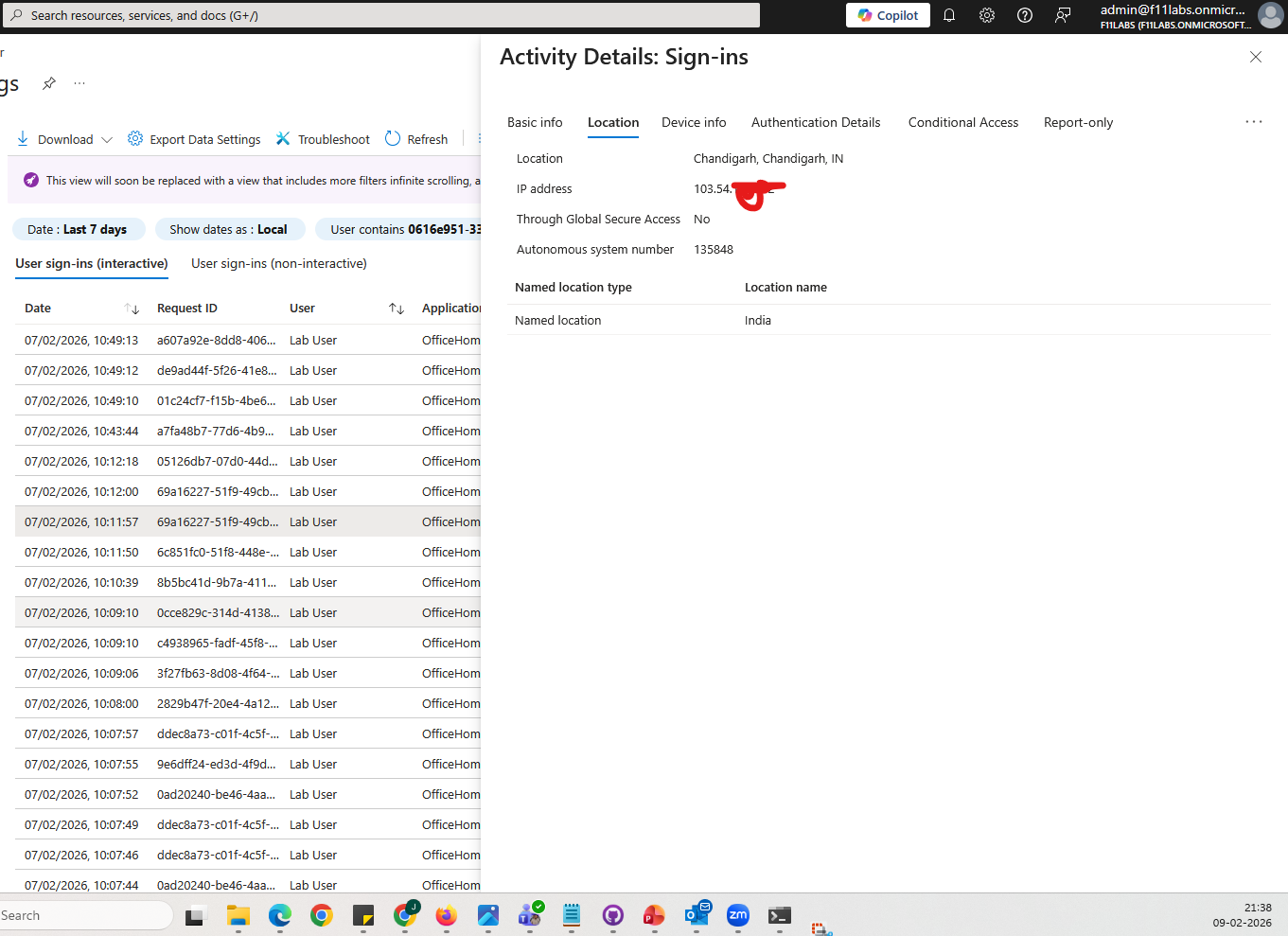
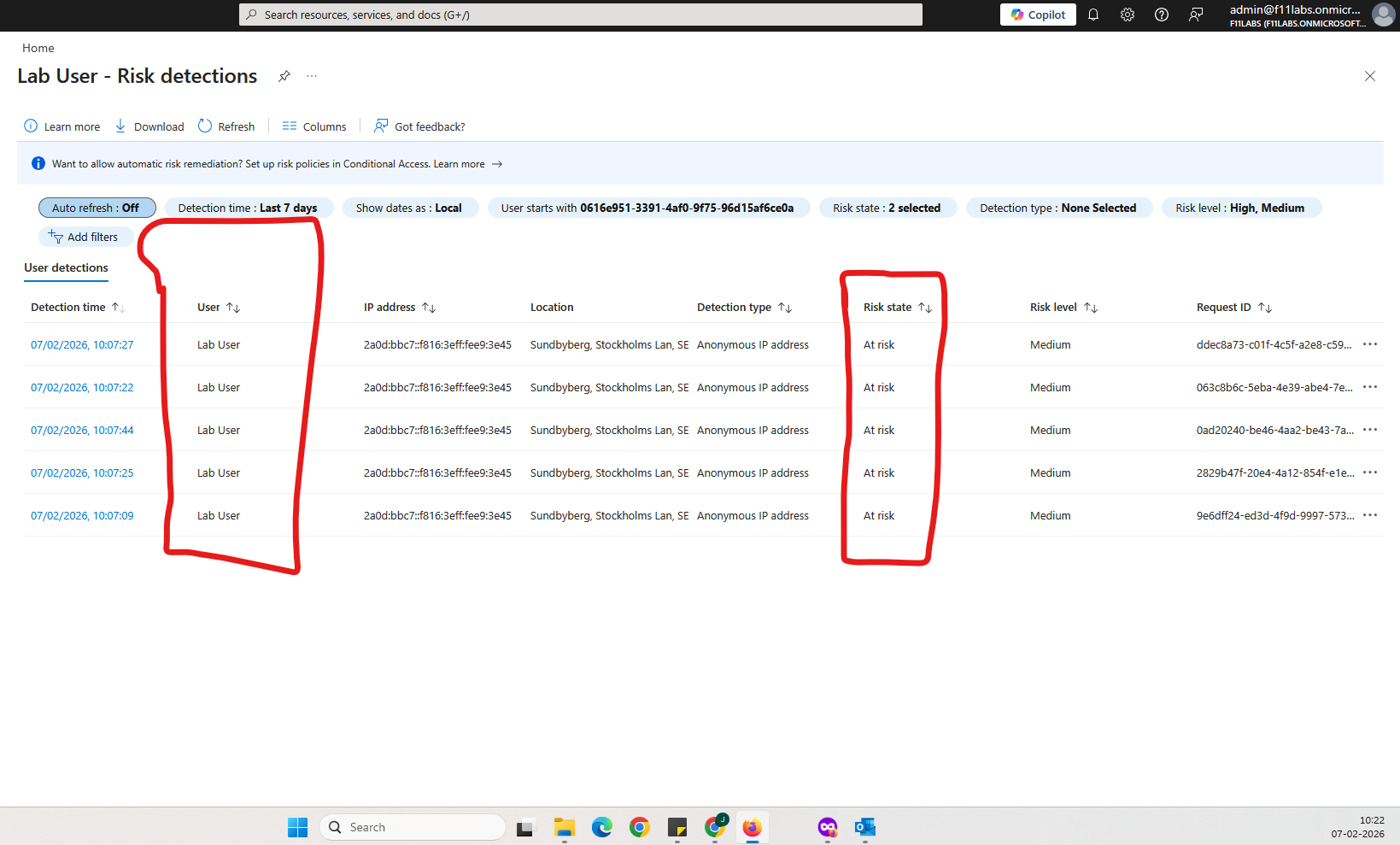
Sign-in logs showing:
- Sign-in status: Success
- Risk level: Medium / High
- Location: unexpected (VPN)
EID-EXP-005-02 — Evidence: User Risk Persists After Risky Sign-in
Control Area
Identity Protection — Risky Users
Expected Secure Behavior
A user flagged as risky should be required to remediate, such as by resetting their password, before regaining access.
Observed Behavior
- User is flagged as at risk.
- User risk remains active.
- The user can continue to authenticate without restriction..
Impact
- The tenant is aware of compromise signals.
- The compromised identity remains active.
- Attackers may continue to exploit the compromised account.
Evidence Artifact
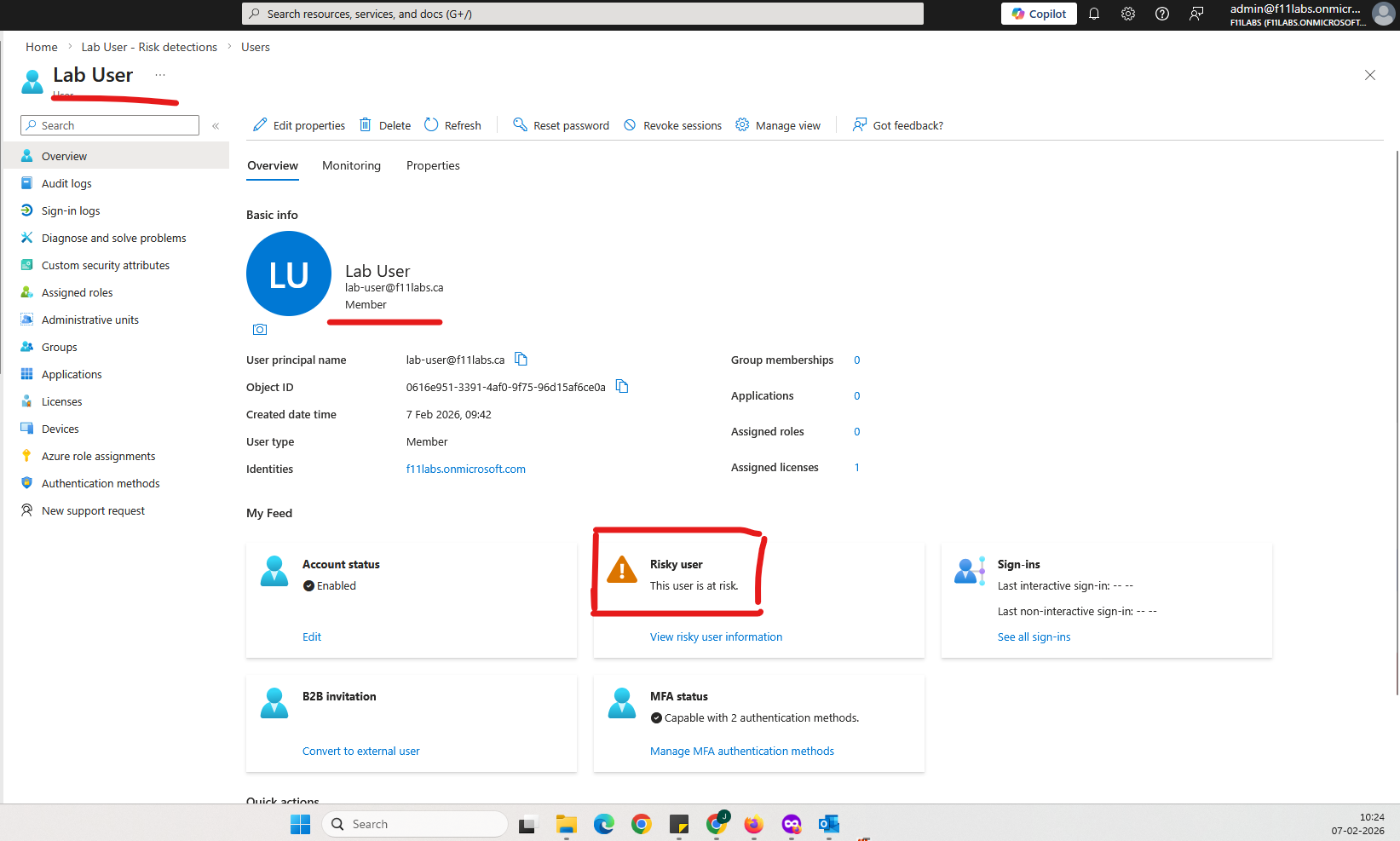
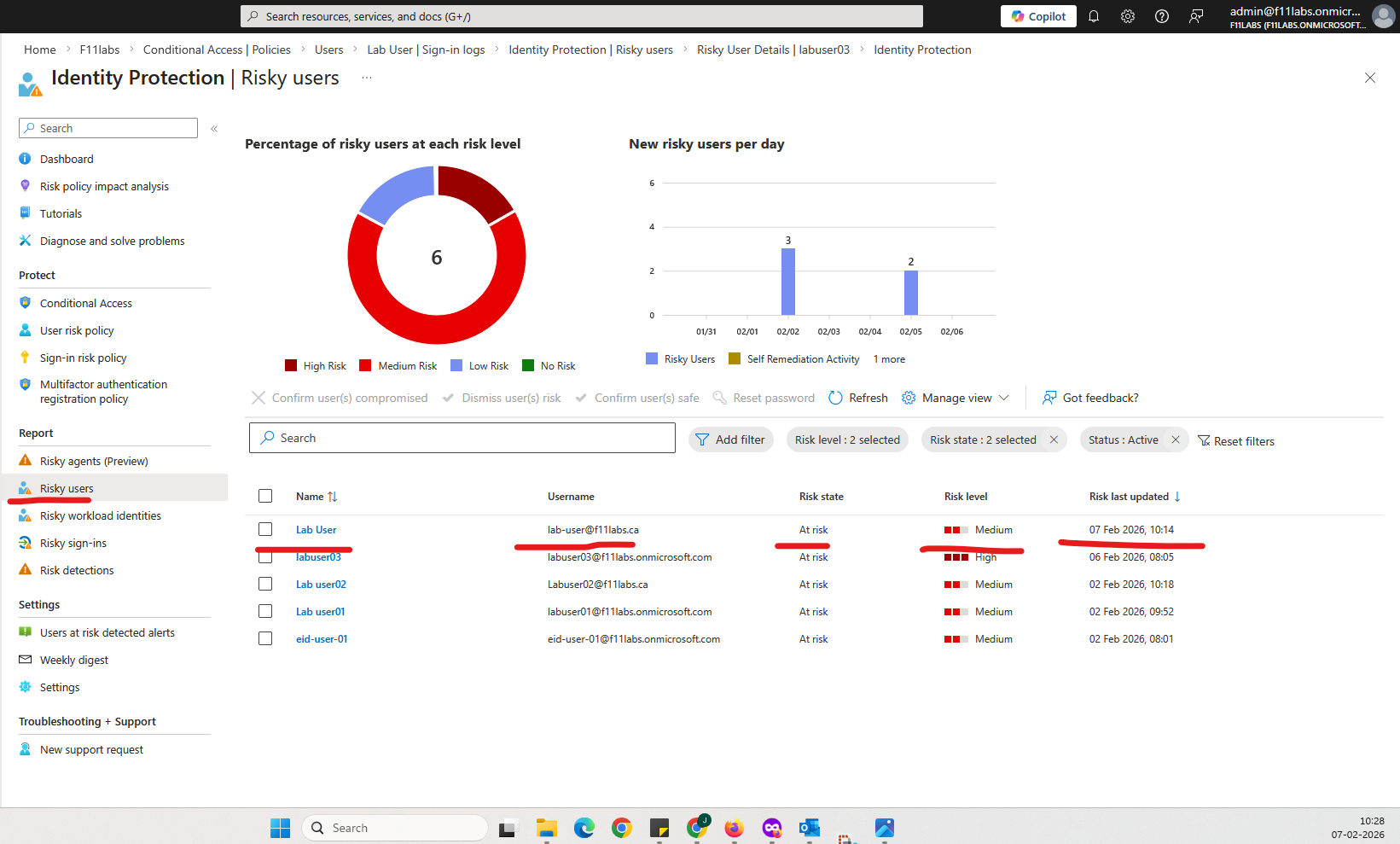
Identity Protection → Risky users showing:
- Risk state: At risk
- Risk level: Medium / High
EID-EXP-005-03 — Evidence: No Risk-Based Conditional Access = No Remediation
Control Area
Conditional Access — Policy Enforcement
Expected Secure Behavior
Risk signals should automatically trigger access controls.
Observed Behavior
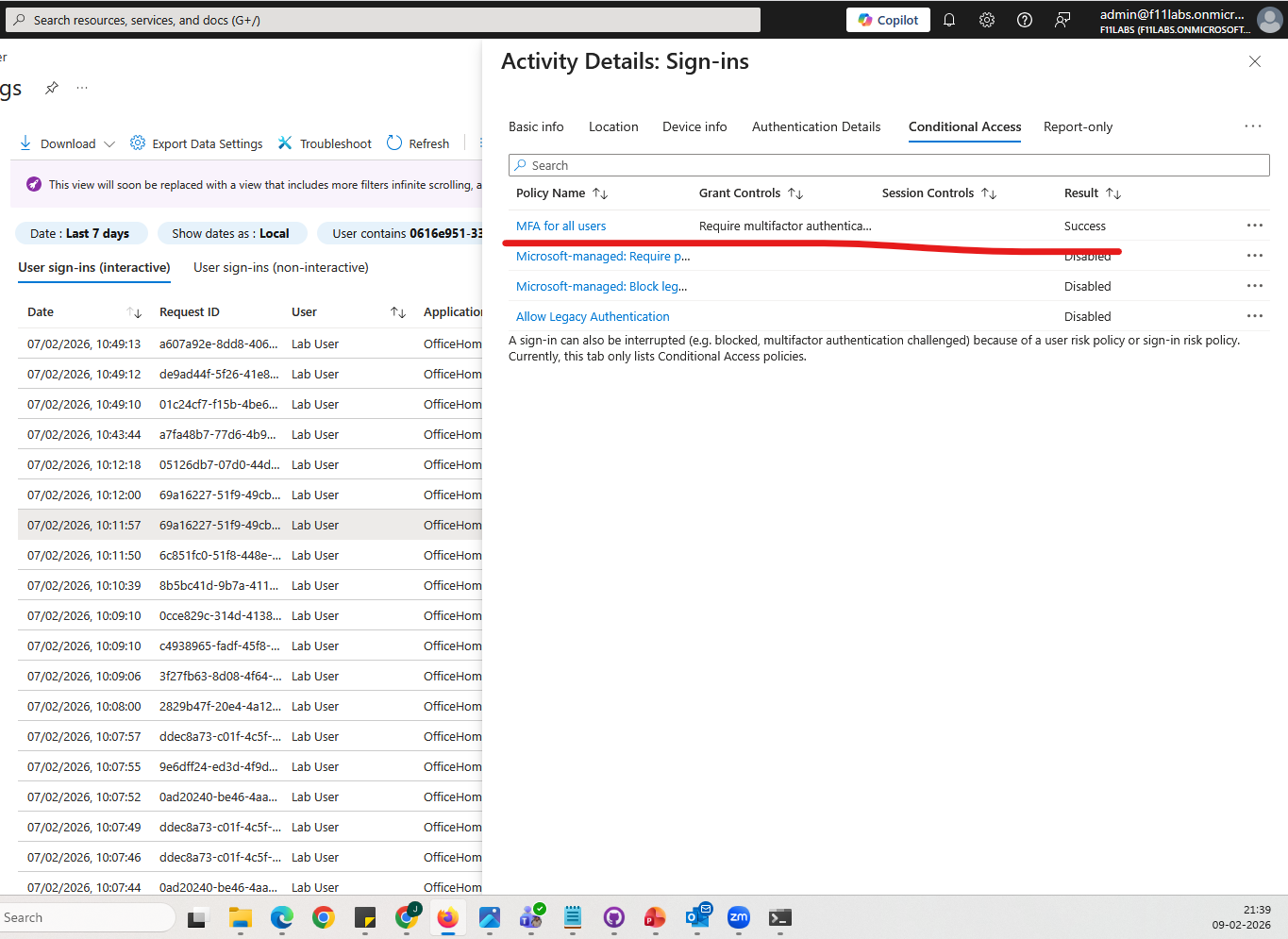
No Conditional Access policies exist for:
- User risk
- Sign-in risk
- Risk signals do not affect authentication outcomes.
Impact
- Identity Protection alerts serve only as informational notifications.
- Administrators may overlook alerts because they do not disrupt user access.
- Compromised identities continue to be active.
Evidence Artifact
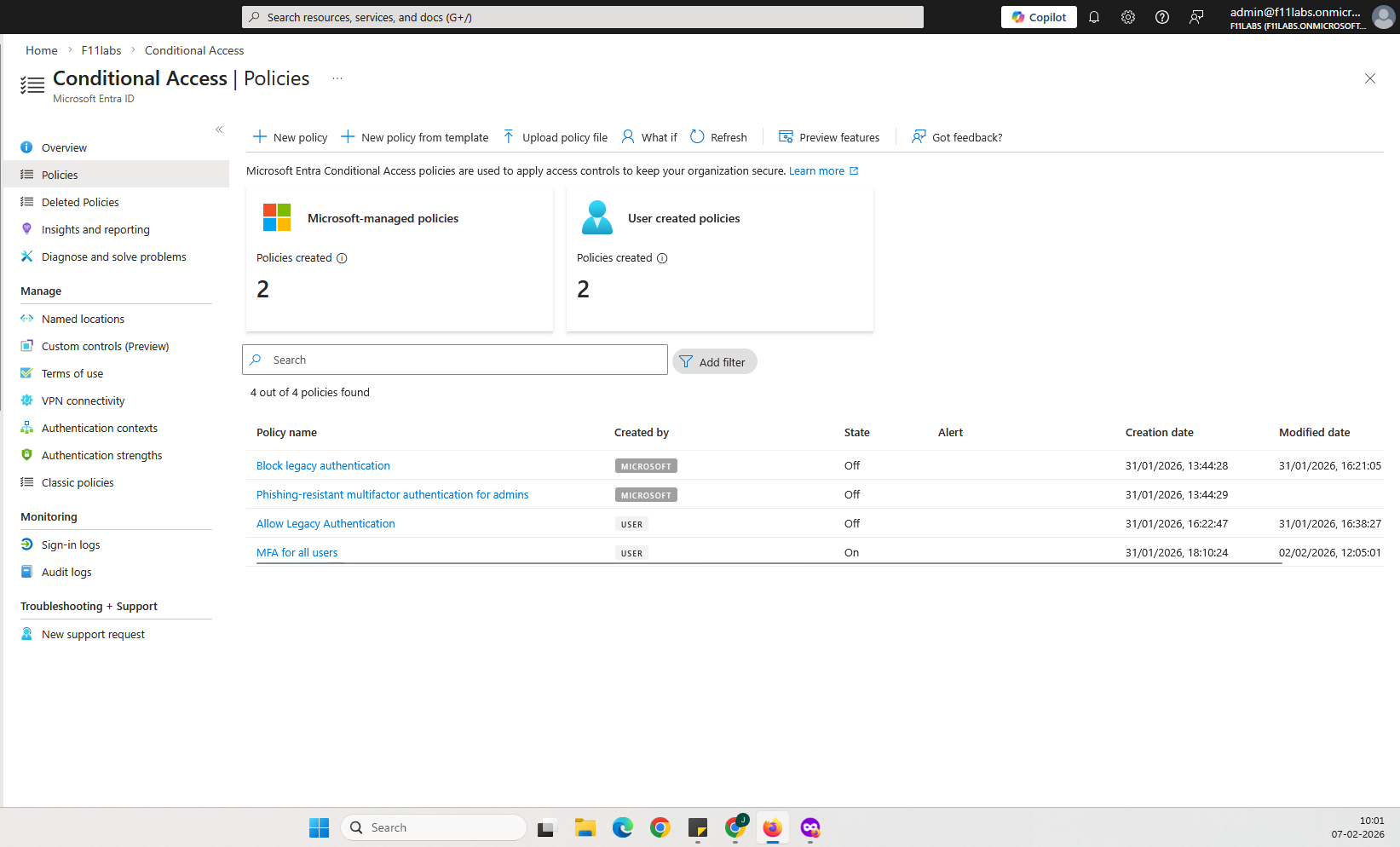
Conditional Access policy list showing:
- No policies configured for risk signals
Remediation (Validated Fix)
EID-EXP-004-04 — Remediation: High User Risk → Require Password Change
Control Area
Conditional Access — User Risk Remediation
Policy Name
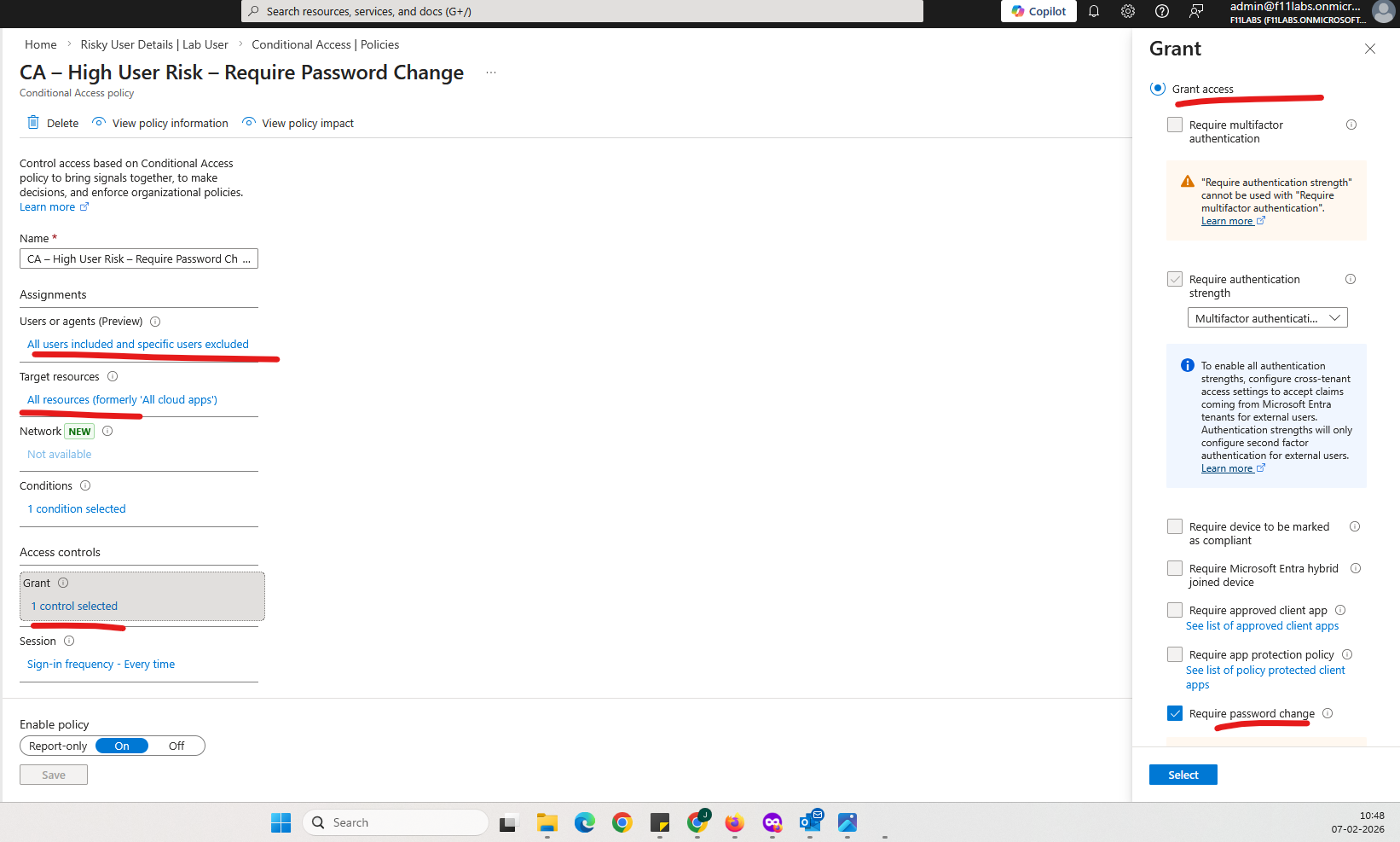
CA – High User Risk – Require Password Change
Policy Configuration
Users
- Include: All users
- Exclude: break-glass accounts.
Conditions
- User risk: High
Access Controls
- Grant access
- Require password change
Observed Behavior
- Risky user attempts sign-in
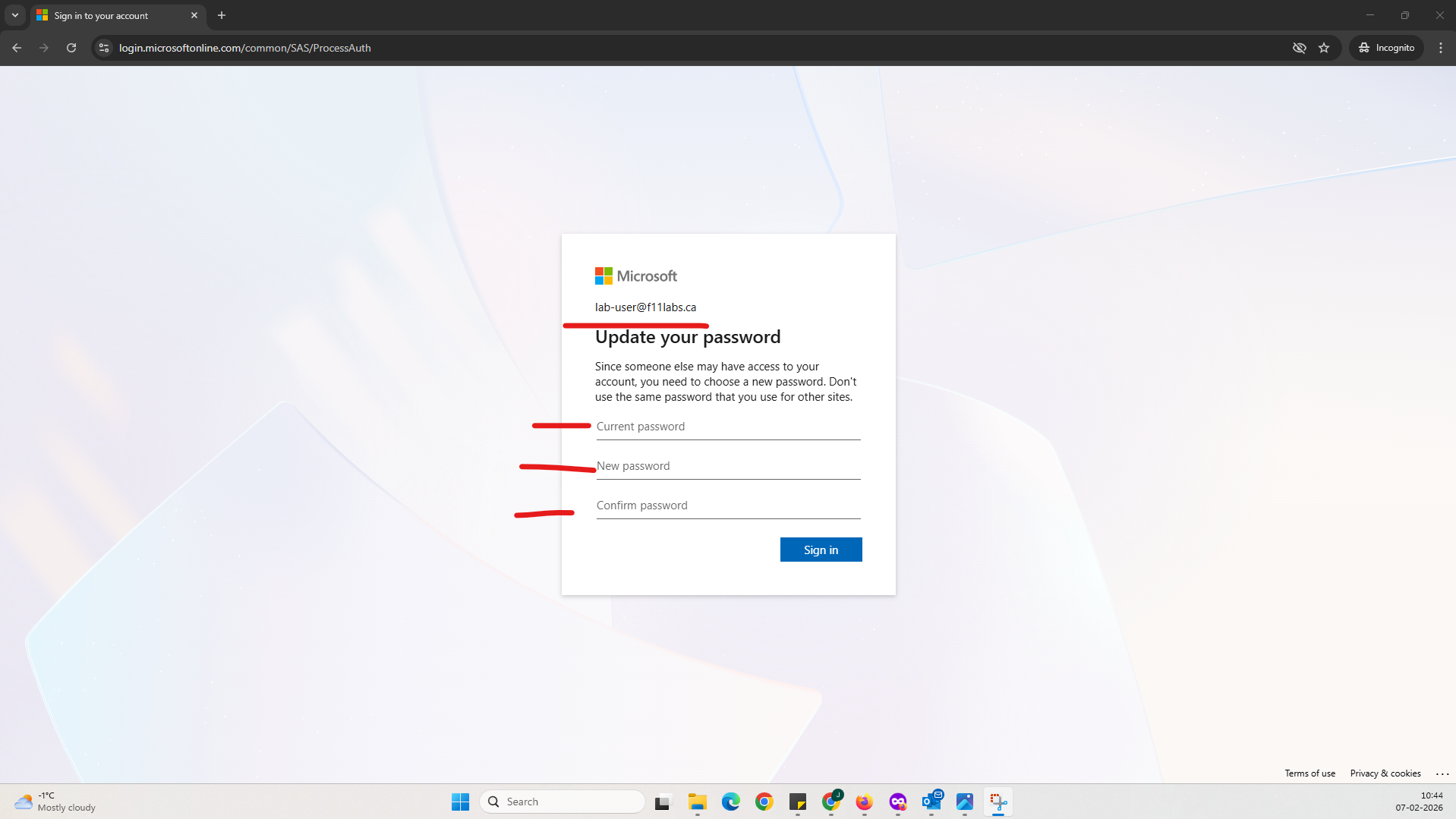
- User is forced to reset the password.
- Access is blocked until remediation is completed.
Impact
- Stolen credentials are neutralized.
- Compromised identity is remediated automatically.
- Risk state is cleared after password reset.
Evidence Artifact
- Sign-in interruption showing password reset requirement
- Risky user state updated after remediation.
EID-EXP-005-05 — Remediation: Medium/High Sign-in Risk → Require MFA (Optional Baseline)
Control Area
Conditional Access — Sign-in Risk Enforcement
Policy Name
CA – Sign-in Risk – Require MFA
Policy Configuration
Users
- Include: All users
- Exclude: break-glass accounts
Conditions
- Sign-in risk: Medium and High
Access Controls
- Grant access
- Require MFA
Observed Behavior
- Risky sign-ins consistently trigger MFA.
- Risky sessions are hardened.
Evidence Artifact
- Risky sign-in event showing MFA required
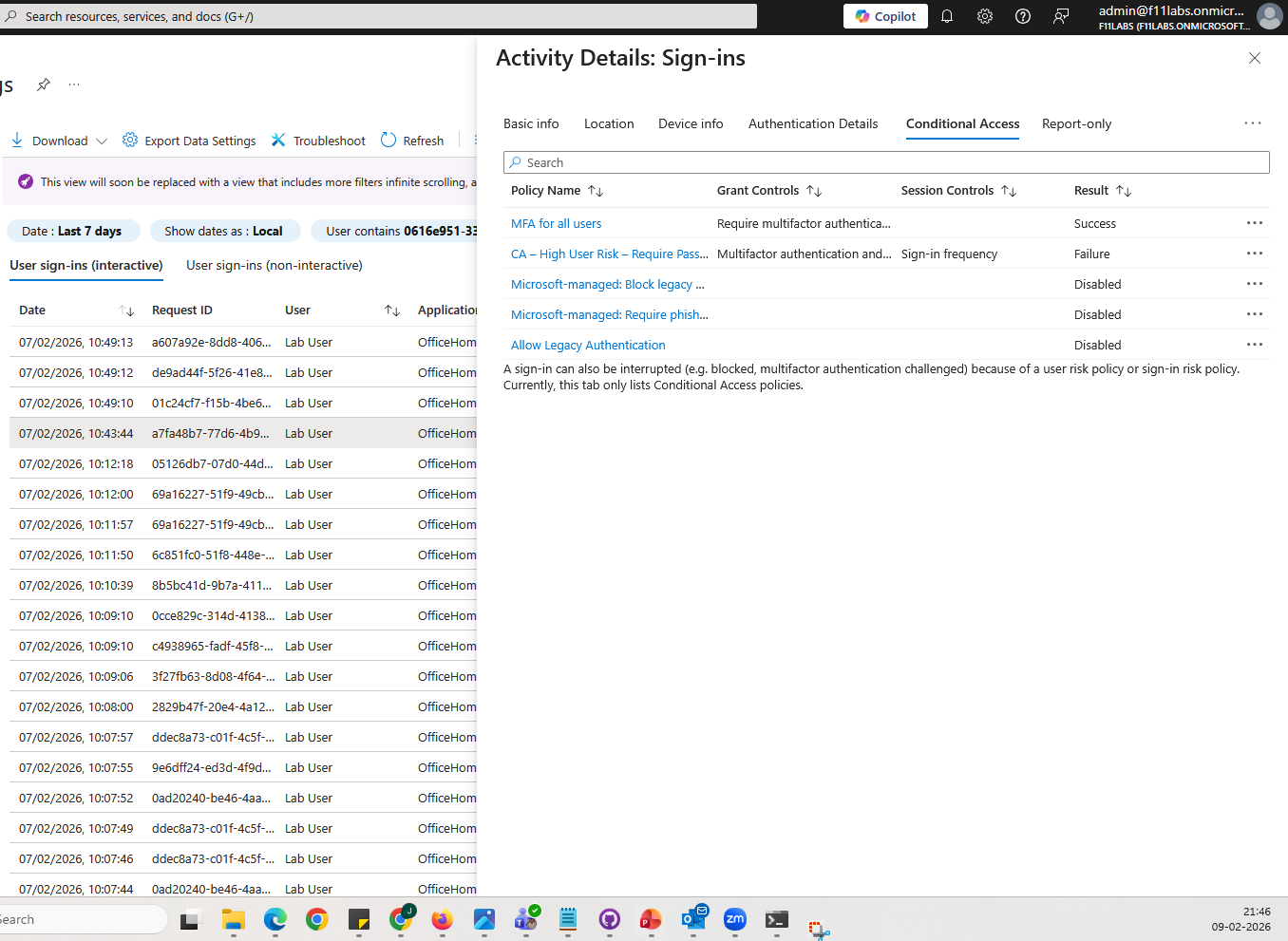
Evidence Summary
| 005-01 | Risky sign-in detected | Sign-in still succeeds |
| 005-02 | Risky user persists | Risk remains active |
| 005-03 | No CA enforcement | Alerts are informational |
| 005-04 | High user risk remediation | Password reset enforced |
| 005-05 | Sign-in risk enforcement | MFA enforced consistently |
Evidence-Based Conclusion
This experiment confirms that:
- Microsoft Entra Identity Protection can detect risky activity.
- Detection alone does not secure the tenant.
- Without risk-based Conditional Access, risky identities remain usable.
- Enforcing password resets for medium and high-user risk is among the most effective identity controls.
Key takeaway:
Detection identifies the issue. Enforcement resolves it.
Next Experiment
EID-EXP-006 — Configure Alerts + Notifications for Risky Users and Risky Sign-ins
Related Analysis & Fix Guidance
- Technical deep dive: Enforcing Risk Remediation in Microsoft Entra ID: Making Identity Protection Actually Stop Attacks
- MSP risk & business impact: Microsoft 365 Identity Protection Alerts Alone Do Not Prevent Attacks, and This Gap Can Be Costly
- Video walkthrough: Entra Identity Protection Doesn’t Stop Attacks — Conditional Access Fix (Evidence Lab)